Let us take a deeper look into how a malicious crypto trader, using a few million dollars, was able to artificially inflate the price of Mango’s ($MNGO) tokens on the Mango Market and withdraw over $116 million from the platform.
What Was Mango Markets:
Mango Markets was a decentralized exchange (DEX) built on the Solana blockchain. Mango attempted to be a one-stop shop for any trader looking for either spot markets, perpetual futures, and lending. Mango allowed cross-margin trading using up to 5x leverage. Mango utilized a margin trading protocol that allowed cross-margin trades between any number of different crypto assets as collateral. Mango used an oracle which brought them the spot prices of these assets from a few exchanges to determine the listed value of the crypto asset on the exchange. The term “oracle” is inspired by the divine truth-telling figures from Greek mythology, which in the case of decentralized finance ( Defi) usually describes the data sources on which smart contracts rely to make decisions. Blockchain oracles are a bridge between the world and the protocol, providing the information the smart contract needs to operate. Here, the oracles were used to identify crypto asset prices and allow for cross-trades and loans.
Here’s a very simple example of a cross-trade, for reference:
- Yesterday, Bitcoin (($BTC) was trading at $16,000 per $BTC. You purchase 1 $BTC.
- Today, BTC is trading at $17,000. You sell $1,000 worth of your BTC.
- Instead of keeping the $1,000, you immediately buy 1 Ethereum ($ETH) (let’s say $ETH is valued at $1,000 per token).
- You have retained your original $16,000 worth of BTC, and now have 1 $ETH as well.
- You have just performed a cross trade.
How Mango Was Exploited:
The Mango exploiter was able to drain nine figures from Mango by manipulation of the price oracle for the $MNGO token, and then utilized the platforms cross-trading abilities to utilize the now “valuable” $MNGO tokens and withdraw other crypto assets (like stablecoins, USDC, USD and $SOL). Lets take a look at how the attacker was able to do this. The entire exploit took place in just 40 minutes.
Attack Flow:
The attacker first funded two wallets with $5,000,000 USDC.
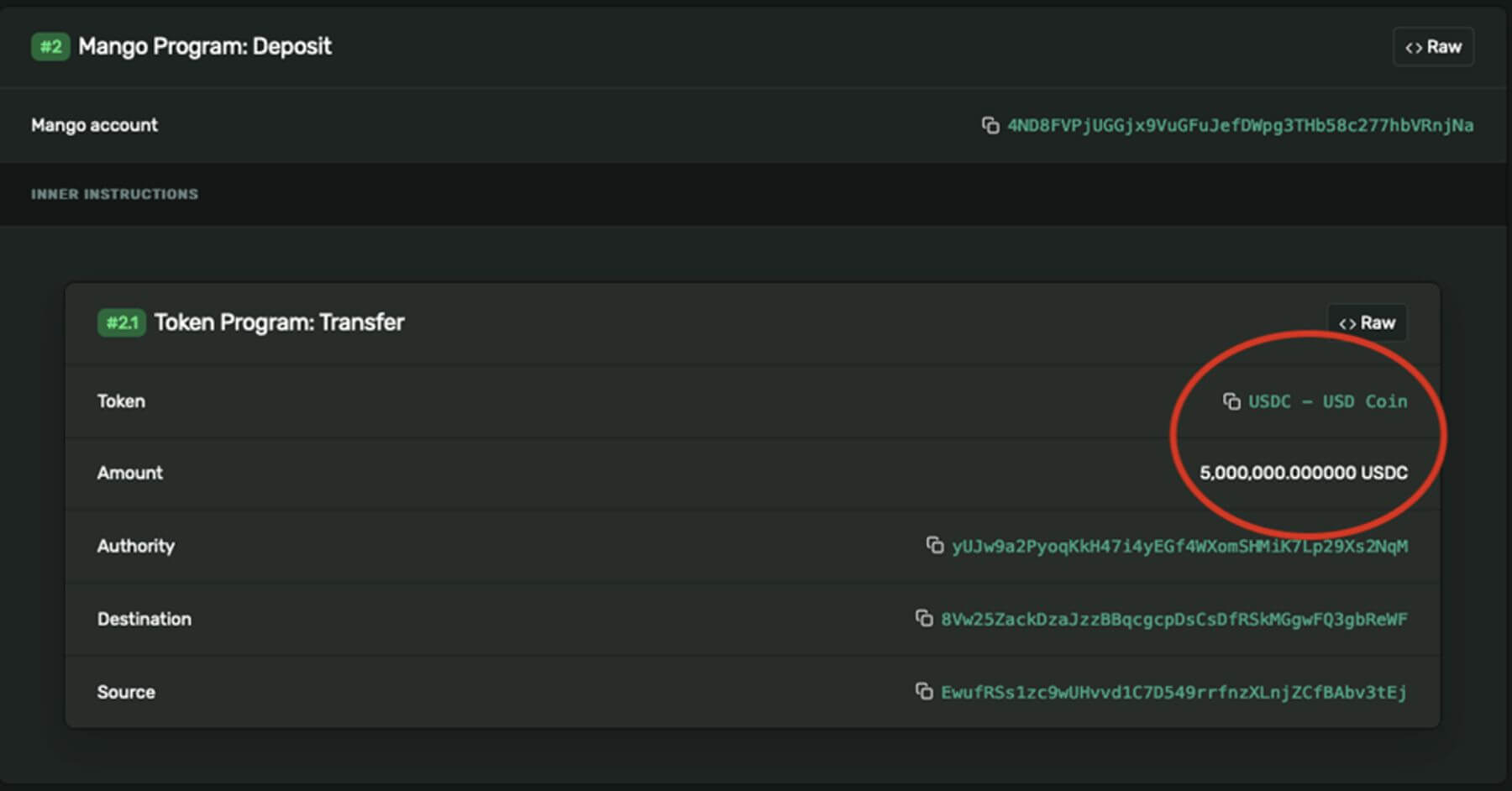
Wallet 1 was funded with 5 million USDC with this transfer.
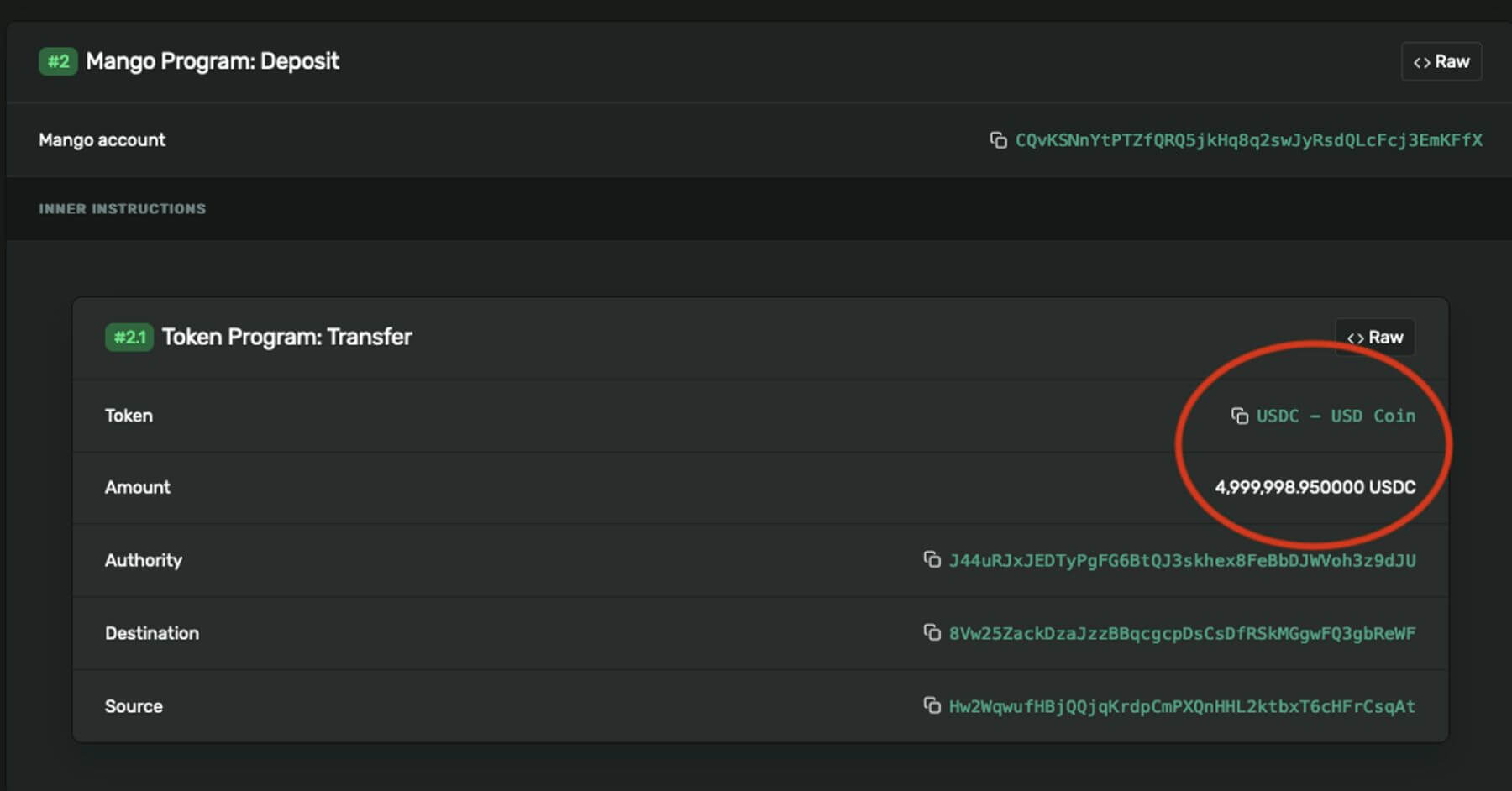
Wallet 2 was then funded with 5 million USDC in this transfer
Wallet 1 then places a sell offer totaling 483 million $MNGO perpetual futures at 3.8 cents per future.
A traditional futures contract in the legacy markets is a type of derivative that allows traders to speculate on the future price movements of an underlying asset. The contract specifies that the trader will buy or sell a specific amount of the underlying asset at a pre-agreed price and delivery date in the future. A future contract and a perpetual futures swap are similar in that they are both derivatives that allow traders to speculate on the future price movements of an underlying asset. A traditional futures contract has a specific expiration date, at which point the contract is settled and the trader must either take delivery of the underlying asset or close out their position. In contrast, a perpetual futures contract does not have an expiration date and rolls over indefinitely. Both futures contracts and perpetual futures contracts offer high leverage, meaning that traders can control a large position with a relatively small amount of capital
In a perpetual future swap, the trader opens a position by putting up a small amount of collateral, which serves as security for the borrowed funds. Perpetual future swaps allow traders to essentially trade with leverage by borrowing funds from the exchange and putting up collateral, magnifying potential gains and losses.
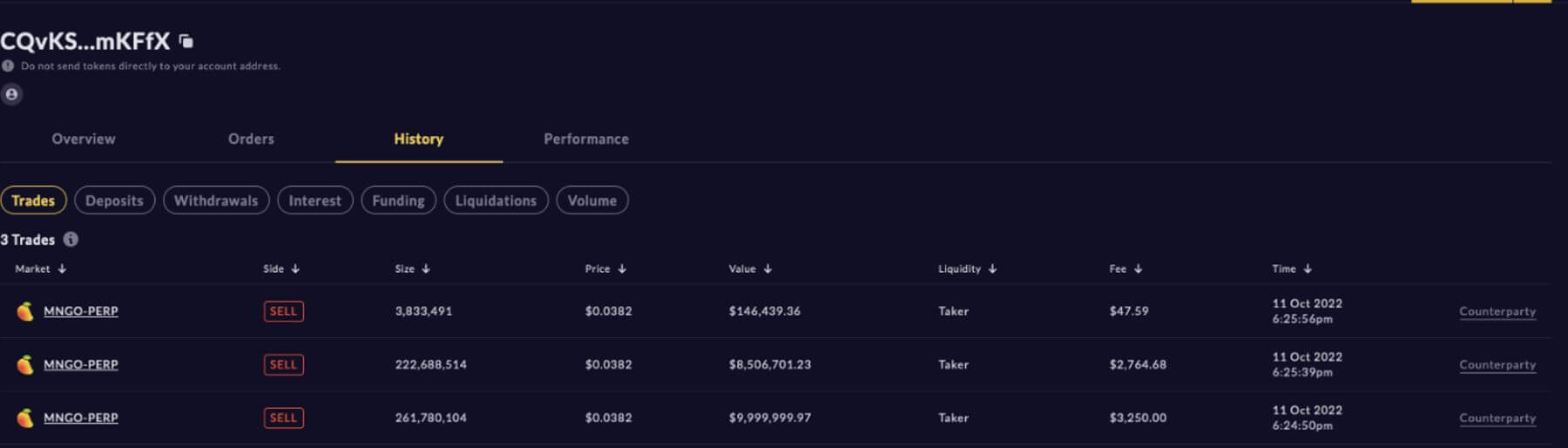
Wallet 2 then purchases all 483 million $MNGO perpetual futures from Wallet 1 at a price of $0.0382 per unit.
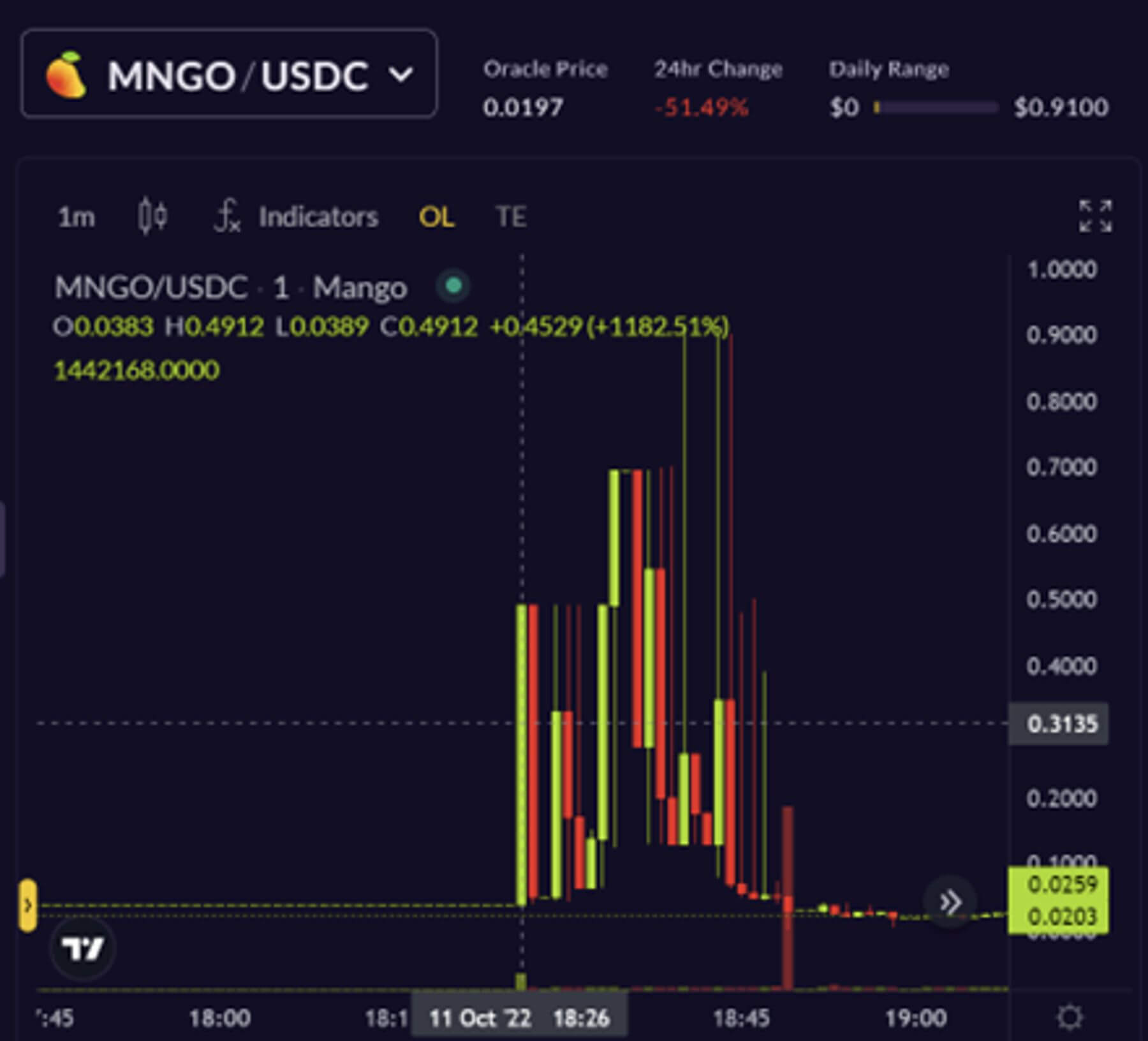
The attacker then starts buying spot $MNGO on multiple exchanges including Mango Markets, AscendEX, and FTX. The price of $MNGO fluctuates wildly peaking at $.91
The attacker settled the profits and losses between Wallet 1 and Wallet 2, giving Wallet 2 a huge unrealized profit from the 483 million long position. Then they utilized this now huge unrealized profit to take out a loan.
The funds were then used to acquire a loan for $116 million using crypto tokens on the platform. The attacker then withdrew the loaned crypto assets using the unrealized profits as collateral. This all took place in just a matter of minutes.
Spot $MNGO prices soon corrected down to 2 cents, falling under the prices that the trader first used to purchase MNGO futures on account Wallet 1. In summary, the attacking trader used a little more than $10 million to extract over $116 million from Mango Markets. They utilized Mango’s trading features within the smart contract’s parameters. Mango Markets was not hacked. It operated as its framework intended, allowing the malicious trader to take advantage of the token liquidity and wipe out Mango Markets.
Post Hack:
The attacker proposed to members of the project’s decentralized autonomous organization (DAO) that they will return the majority of the loot if the community agrees to repay bad debt that was taken during a June operation to save a different Solana project called Solend. In response, the project team created their own proposal on Oct. 14. As per the proposal, the attacker will return up to $67 million and keep the remaining $47 million as essentially a bug bounty. The proposal also states that they will “waive any potential claims against accounts with bad debt, and will not pursue any criminal investigations or freezing of funds once the tokens are sent back as described above.” Mango tweeted on Oct 15th that $67M in various crypto assets were returned to the DAO.
One of the attackers voluntarily came out and announced himself as the exploiter in a series of tweets, claiming that he operated within the framework of the protocol and that it was “a highly profitable trading strategy” and that it had been “legal open market actions, using the protocol as designed.”
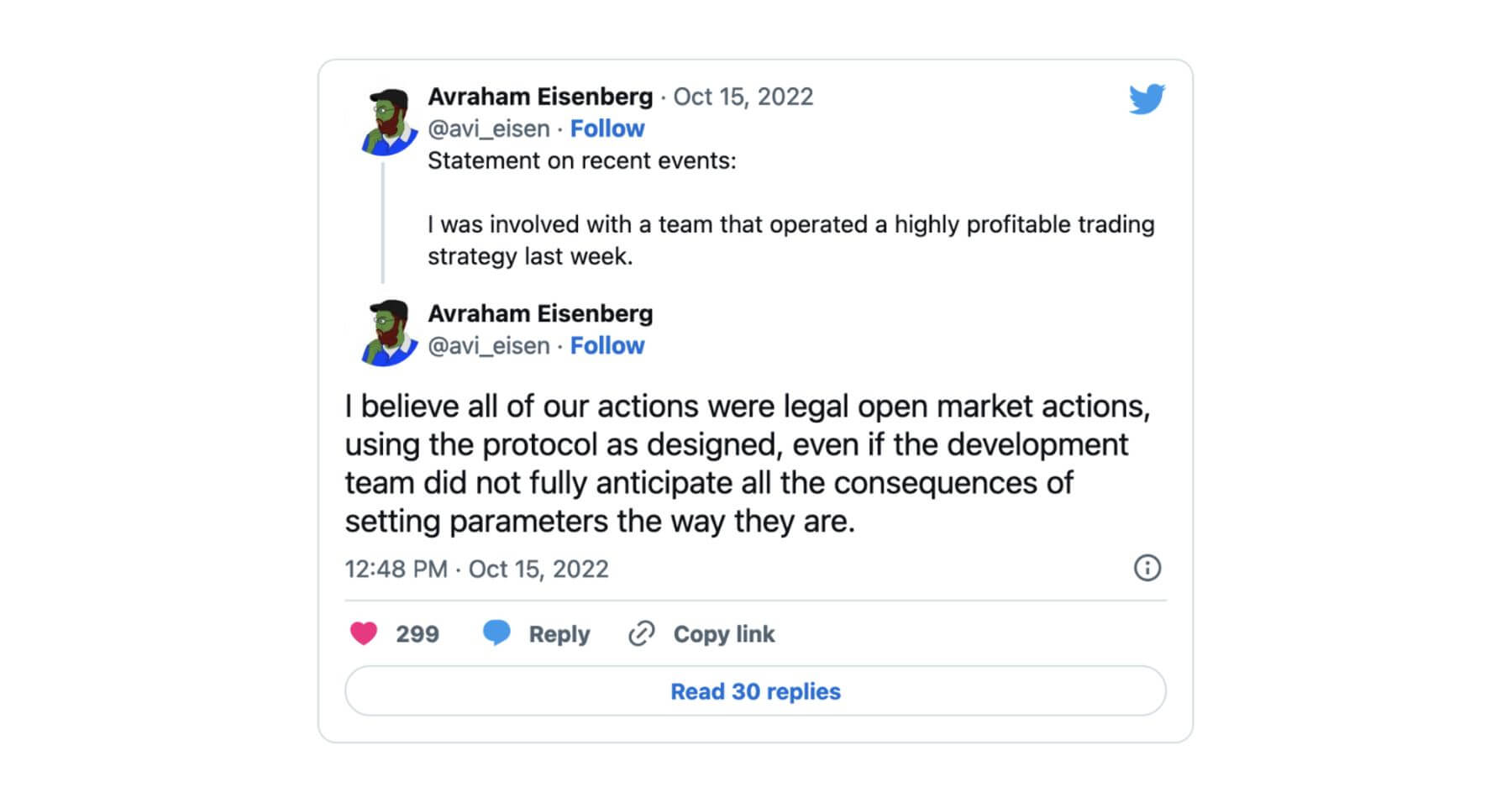
Not everyone seemed to agree however, as he was arrested and charged with market manipulation offenses in the Southern District of New York.

Mango Markets also filed a Civil Suit on January 25th against Eisenberg, accusing Eisenberg of a “brazen attack” that included causes of action for conversion, fraudulent misrepresentation, and unjust enrichment. The complaint alleges that the agreement entered into between the DAO Eisenberg was made under duress and should not be enforceable. Mango Markets is seeking $47 million in damages and interest, starting from the date of the attack. This civil suit is interesting, because there has been limited case law precedent for DAOs as they are a relatively new concept in the world of law. DAOs have been designed to be decentralized and self-governed, which can make it difficult to determine jurisdiction and accountability in the event of disputes. As the use and popularity of DAOs continue to grow, it is likely that more legal cases will emerge and establish precedent. Watching whether the court chooses to address the topic will be interesting.
What Can We Learn From This Mango Exploit:
Oracles Are Not Infallible:
Price manipulation attacks have been a longstanding issue in the DeFi space. During the DeFi boom of summer 2020, when oracles were not yet widely used in the space, numerous protocols were attacked and had their treasury funds removed by attackers who would inflate the value of an illiquid token, (such as the protocol’s own token). Allowing them to withdraw standard crypto assets like $ETH. The protocols back then mainly used price feeds from one exchange, making it easier to manipulate the value. Defi protocols since then have been relying on oracles to determine a crypto asset’s price. Mango Markets utilized oracles to calculate the price of an asset by using a moving average of centralized exchange price feeds. Here the oracle accurately reported the current price of $MNGO, by using the moving averages from a few exchanges to allow borrowing against it on Mango Markets. It’s just that the price of $MNGO at the time of the exploit was manipulatively inflated for just enough time for the attacker to borrow a tremendous sum against this temporarily inflated price.
A key takeaway for DeFi protocols is to understand that incorporating price oracles into their Defi protocols doesn’t mean that the protocol is now infallible just because the oracle is averaging prices from multiple sources. In this case, the illiquid token was able to be pumped up with a relatively minimal amount of money. To ensure accuracy and integrity, an oracle should continuously assess the quality of the market it is monitoring and exclude venues that may be vulnerable to manipulation by establishing clear exclusion criteria.
Chain Monitoring:
DeFi protocols have operated under a “code is law” mantra. To effectively combat market manipulation, DeFi protocols and DEX’s should place a higher value on trade monitoring approaches that can identify and alert upon unusual price or volume activity. Had there been such a system in place it’s quite possible that these transactions would have been flagged. The circulating supply of $MNGO was 1 billion, so a perpetual contract that was opened for 483 million (or almost half the circulating supply) would have immediately been flagged. Or if there were limits on the open interest say at 50 million (which would only be 5 percent of the total circulating supply) the attack would not have been profitable.
As others alluded to, Mango protocol charged zero fees. As a result, the protocol did not have an insurance fund. “When a margin account has negative equity, the losses are socialized among the lenders. There is obviously the risk that a user loses his margin account to a liquidator when his account goes below the required maintenance collateral ratio (MCR) of 110%. But there is an even bigger risk to the ecosystem when a margin account falls below 100% collateral ratio. At this point, the value of the account’s liabilities are larger than the value of assets.”
DeFi protocols are still in their infancy, but to avoid situations like this in the future, protocols may have to implement a range of potential solutions. Making the oracles they use “smarter”, limiting (or avoiding leverage) with assets that have low liquidity. Having chain monitoring and transaction flagging processes in place, and other potential solutions will be integral in mitigating the risk of market exploits in the future.
Disclaimer: This article was written on February 1st, 2023 and any events, developments, or information that may occur after this date are not included in the content of this article. The information contained in this article is accurate as of its publication date and may no longer be up-to-date or relevant in the future.





