In Part 1, we explored the origins and evolution of best execution, along with the rise of decentralized exchanges and aggregators in the crypto sector. Now we’ll dive deeper into the complexities of Maximal Extractable Value (MEV) and recent exploits that have rocked the DeFi sector.
Part 2: MEV and Recent Exploits
At its core, MEV refers to the additional profits block producers can extract from their ability to arbitrarily reorder transactions within the blocks they produce. Transactions on public blockchains, like Ethereum, are not inherently ordered. It is up to the block producers constructing blocks to sequence transactions how they choose.
Block producers are incentivized to maximize profits from the transactions they verify. One way they can do this is by analyzing the pending transaction pool (mempool) and selectively reordering, including, or excluding transactions in ways that are financially advantageous.
Some common MEV strategies block producers employ include:
- Front-running: Detecting a large pending trade on a DEX and rushing to place their own buy/sell order just before it executes.
- Sandwich attacks: Placing buy orders before and sell orders after a pending DEX trade to artificially inflate or deflate the price against the target.
- Liquidations: Reprioritizing transactions to liquidate users’ collateralized positions on lending platforms earlier.
- Arbitrage: Ordering transactions across DEX platforms to capitalize on temporary price inefficiencies.
By extracting MEV, block producers are able to earn extra profits on top of the standard block rewards and gas fees. However, these strategies introduce risks like unexpected price volatility, failed transactions, and general loss of ecosystem integrity. There are numerous initiatives focused on mitigating and combatting MEV, but for now, MEV remains a challenge undermining aspects of decentralization and transparent execution in DEX trading.
A notable MEV bot is “jaredfromsubway.eth,” named tongue-in-cheek after the former Subway spokesman Jared Fogle. An analysis of transactions linked to this Ethereum address revealed that in just three months, this MEV bot accumulated over $6.3 million in profits by executing sandwich attacks on DEX trades. The complexity, combined with the rapidly evolving legal landscape for cryptocurrencies, contributes to the challenge of determining the legality of these practices.
Here’s a step-by-step breakdown of how a sandwich attack happens on-chain:
- Spotting the Target Transaction: The attacker monitors the mempool and spots a large pending DEX trade.
- Initiating the Attack: The attacker places a buy order with a higher gas fee to ensure it gets processed before the target transaction. This is the “front” of the sandwich.
- Price Manipulation: The attacker’s buy order drives up the token’s price on the DEX.
- Target Transaction Execution: The trader’s transaction (the one spotted in the mempool) gets executed. However, due to the attacker’s buy order executing ahead of the trader’s buy order, the trader ends up buying the token at the inflated price.
- Completing the Sandwich: After the trader’s transaction is executed, the attacker immediately places a sell order, again with a higher gas fee to ensure swift processing. This is the “back” of the sandwich. The sell order brings the token’s price back down, often lower than its original price before the attack.
- Profiting from the Attack: The attacker profits from buying low and selling high around the target trade’s execution.
Alternative Transaction Ordering: Sandwiching
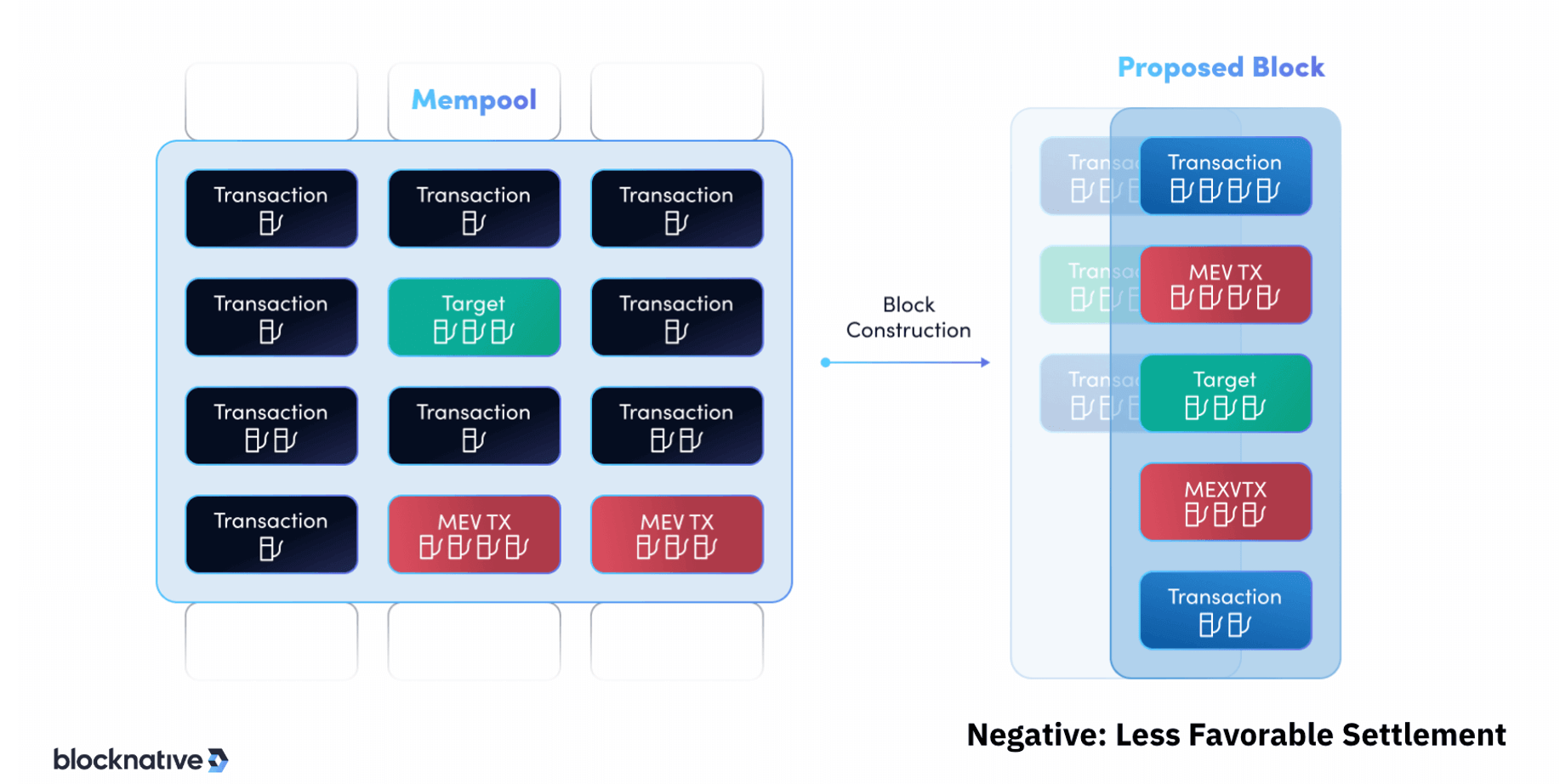
The presence of advanced MEV bots sniffing out arbitrage and exploitation opportunities leads to unexpected price volatility on DEX platforms. When these bots spot a potentially lucrative trade, they scramble to push through transaction reordering on the underlying blockchain to profit. This causes erratic price spikes and crashes as the bots trade against the pending transactions. For regular traders on DEXs, these rapid manipulations by MEV bots lead to increased slippage between the expected trade price and the actual execution price. The volatility makes it extremely difficult for traders to reliably transact at their intended prices and terms, which negatively impacts best execution.
This phenomenon can be likened to traditional equity automated trading, where algorithms and high-frequency (HFT) trading strategies are employed to gain advantages in the market. MEV bots and HFT bots both prioritize speed to capitalize on market inefficiencies. MEV bots observe and act on pending transactions in the mempool, while HFT bots detect and act on large orders in traditional markets. Technological advantages, from superior algorithms to infrastructure, play a pivotal role in both domains. Despite operating in different environments, both face regulatory scrutiny and ethical debates due to concerns about market fairness and potential destabilization.
Curve Finance Exploit
Up until this point, MEV has been painted with a negative stroke, but let’s explore a recent event leveraging ethical MEV strategies. In July 2023, Curve Finance was hacked, resulting in an estimated $60+ million worth of funds drained from the protocol. Curve Finance is a leading DEX with a focus on stablecoin swaps.
The breach exploited a reentrancy vulnerability within Curve’s factory pools, including the CRV-ETH pool, the most liquid liquidity pool for the CRV token. Reentrancy arises when an interrupted contract function can be called again recursively before the first invocation completes execution. The hacker made repeated recursive calls to rapidly drain funds before balances updated. A more technical explanation for reentrancy attacks can be found here.
As an analogy, imagine you’re at an ATM, and you request to withdraw $100 from your account. The ATM follows a two-step process:
- Deduct $100 from your account balance.
- Dispense $100 in cash.
Now, let’s say there’s a glitch in this ATM. After it starts the process of dispensing the $100, but before it completes the deduction from your account, you quickly request another withdrawal. The ATM, due to its glitch, starts dispensing another $100 without first checking or updating your account balance. You could potentially withdraw more money than you have in your account, all because the ATM didn’t finish its first task before starting the second one. In the smart contract scenario, this is similar to how a reentrancy vulnerability is exploited. An attacker can interrupt a transaction midway and start a new one, taking advantage of the fact that the contract hasn’t updated its state or balance from the first transaction.
The root cause was traced to an outdated Vyper contract language version that failed to adequately secure transaction states. Vyper is a smart contract programming language that closely resembles Python in its syntax. Created specifically to simplify and enhance the safety of writing smart contracts, Vyper has been embraced extensively by the Curve ecosystem.
As the hack continued, a white hat hacker known as “c0ffeebabe.eth” took countermeasures. Leveraging MEV strategies, the white hat hacker front-ran the attacker to secure $5.4 million in ETH and promptly returned it to Curve Finance. This demonstrated how MEV techniques can potentially be deployed ethically to protect protocols.
Following the exploit, Curve Finance founder Michael “Mich” Egorov, who holds the majority of CRV’s circulating supply, has taken out loans against his CRV holdings. Mich began repaying this debt across several lending protocols through a series of over-the-counter (OTC) deals.
These actions have raised liquidation risks around CRV, sparking contagion concerns across decentralized finance. On one hand, transparency in DeFi enables the community to monitor risk exposures across protocols, assets, and key individuals like Mich. This can facilitate stability by allowing preemptive risk management.
However, full transparency can also accelerate volatility in times of crisis. By revealing Mich’s need to repay debts, for example, some may preemptively dump CRV, fearing his holdings could get liquidated and flood the market. This selling pressure further depresses CRV’s price, increasing liquidation risks and necessitating more selling.
This devastating exploit combined with the prevalence of MEV strategies underscores the risks and opportunities facing the rapidly evolving DeFi sector. The emergence of decentralized finance has opened up new possibilities for peer-to-peer financial transactions. However, as outlined in this two-part blog, it has also introduced complex risks and challenges that can undermine best execution for market participants.
——-
Disclaimer: This blog was written in August 2023. The information contained herein is accurate as of its publication date and may no longer be up-to-date or relevant in the future. Always consult with a financial professional before making any investment decisions.